The provision of devices is one of the central tasks in IT administration. Until a few years ago, however, this process was extremely time-consuming. Setting up, for example, a new laptop or PC for corporate users required physical space to store the devices as well as an infrastructure to create and maintain device images.
Since its launch in 2017, Microsoft has developed Windows Autopilot, a solution that simplifies and standardizes device deployment. In the summer of 2024, Microsoft released a completely outdated version under the name Autopilot Device Preparation, so that many people talk about Windows Autopilot V2. But what exactly is the difference between the two versions and how do they prove themselves in practice?
This article provides an in-depth analysis of the features of Windows Autopilot 1.0 and 2.0. We examine both the strengths and weaknesses of the respective versions and discuss which deployment scenarios they are suitable for.
The most important things in brief
- Windows Autopilot is a cloud-based solution for automated deployment and management of Windows devices.
- Windows Autopilot V1 impresses with basic automations such as self-deployment mode, hybrid support and integration with existing infrastructures, but has limitations in terms of flexibility and compatibility.
- Windows Autopilot V2 offers a modernized architecture without hardware hashes, optimized OOBE, real-time monitoring, and advanced app delivery options, but still without hybrid support or pre-provisioning.
SOFTTAILOR helps you implement Windows Autopilot — regardless of whether you're planning a strategy for the transition to V2, optimize existing infrastructure, or want to make the best possible use of future updates.
1. Zero-Touch Deployment with Windows Autopilot
Windows Autopilot is a cloud-based solution from Microsoft that helps companies automate and standardize the deployment and configuration of Windows devices. It enables efficient, user-focused deployment without IT staff having to physically interact with devices. In other words Zero-touch deployment.
The idea behind Autopilot is to replace the classic process of device deployment, which was often characterized by manual steps. Traditionally, IT departments had to prepare devices first, create images, and install them on every device. To do this, it was necessary to connect the device to the corporate network and therefore have it physically on site. New devices could therefore not be issued directly to the end user.
With Autopilot, this task is simplified through a cloud-driven approach. Devices can be configured for use directly from the factory and delivered to end users without detours.
How does Windows Autopilot work?
Windows Autopilot enables automated configuration of devices directly from the cloud as soon as they are switched on for the first time. When you start for the first time, the device automatically downloads all required configurations, policies, and applications. User profiles are automatically assigned, software and security solutions are installed, and the device is directly integrated into existing management systems, such as Microsoft Intune, integrated. This significantly reduces the workload for IT departments, as devices are delivered ready for use from the factory.
The key benefits of Windows Autopilot are efficiency, flexibility, and scalability. IT staff save time by eliminating the need for manual installations or creating images. At the same time, Autopilot allows devices to be made available regardless of the location of end users. The solution is also suitable for companies of all sizes, as the process is fully automated and easily scalable.
2. Windows Autopilot 1.0 (V1): The basics
Windows Autopilot 1.0 was introduced in 2017 and laid the foundation for automated deployment of Windows devices. The aim was to simplify the complex and error-prone process of manual device deployment. By integrating with Microsoft Intune and others Endpoint Management For the first time, companies were able to use a cloud-based approach to make new devices ready for use immediately after delivery.
Key features of Windows Autopilot 1.0
- Self-deployment mode: Devices could be set up without physical intervention by IT staff.
- User assignment: Automatically link devices to specific user accounts or groups.
- Policy and app deployment: Company policies and standard applications were automatically installed during initial setup.
- Easier management: Devices could be connected directly to Microsoft Intune or other management solutions.
Limitations and challenges
Although Windows Autopilot 1.0 offers numerous innovative features, there are still some limitations that are relevant in practice. It is important that Autopilot V1 remains active and is developed in parallel with the new version to cover different requirements.
- Limited hardware support: Many older devices are not compatible with Autopilot V1. More details about the exact hardware requirements can be found in Microsoft documentation.
- Standardised processes: Autopilot is primarily suitable for standardized processes. Organizations with individual requirements or complex network configurations quickly reach limits here. For example, companies with strict security requirements often require special network or VPN configurations that cannot be mapped directly via autopilot. IT staff must then use supplementary solutions or make manual adjustments.
- Dependence on stable Internet connection: A reliable Internet connection is absolutely necessary for initial deployment. In environments with poor network connectivity, this can be a problem.
These weaknesses are being addressed by Microsoft as part of parallel development, with the new version (Autopilot Device Preparation) supporting cloud-first strategies in particular, while Autopilot V1 remains specifically optimized for hybrid or specific IT environments.
3. Windows Autopilot 2.0 (V2): The evolution
With the introduction of Windows Autopilot V2 or Autopilot Device Preparation Microsoft has once again fundamentally rethought device deployment and re-engineered Autopilot V2. This release is based on a newly developed architecture that provides greater flexibility, better scalability, and a streamlined user experience. While V1 was still heavily reliant on registering devices in the cloud, V2 goes one step further and uses a more seamless process that simplifies many existing processes.
Major new features in Windows Autopilot V2
No hardware hash required
With Windows Autopilot V2, there is no need to register devices via hardware hashes. Instead, device management is carried out directly via Entra ID (formerly Azure AD) and MDM policies when you start the device for the first time. This significantly reduces administrative costs and simplifies the procurement process for hardware suppliers. However, the basic requirements for hardware and a reliable Internet connection remain in place.
Redesigned out-of-box experience (OOBE)
The new OOBE in Autopilot V2 provides end users with a clearer progress bar, but progress is updated gradually rather than continuously. In addition, pages such as the End User License Agreement (EULA) and the choice between private and business use are displayed.
Improved real-time monitoring
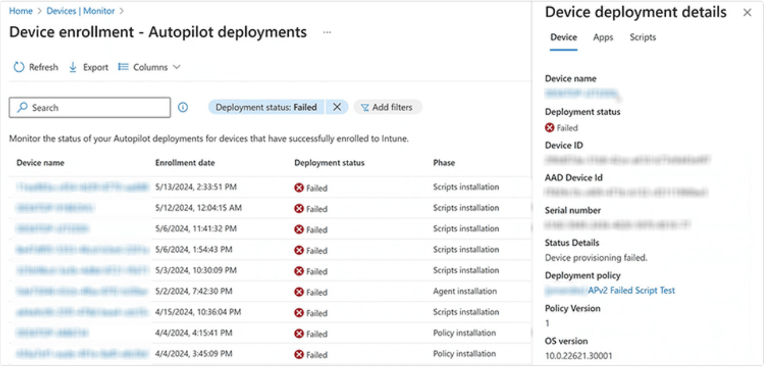
Autopilot V2 provides IT administrators with almost real-time monitoring with a minimal time delay of approximately five seconds. This gives administrators detailed insights into which configurations have already been successfully applied or whether deployment issues have occurred.

Combining MSI and Win32 apps
Unlike Windows Autopilot V1, MSI and Win32 apps can be easily combined in V2. Intune automatically installs MSIs first, followed by PowerShell scripts and Win32 apps.
Optimized app delivery
Administrators can determine which apps should be installed during OOBE and which are added in the background after deployment is complete. This prioritizes important applications such as Microsoft Defender and ensures that devices are up and running faster.

Sovereign cloud support
Autopilot V2 supports government and sovereign cloud environments for the first time, as the new architecture is no longer limited to the public cloud. For now, this is limited to US sovereign clouds.
New user interface design
The interface has been modernized and streamlined, which improves usability. All settings are made on a single screen, making management easier. Devices are now assigned to groups faster and more efficiently. The option to define default admin users is retained. Overall, the workflow remains similar to Windows Autopilot V1, but with a better overview.

Known limitations of Autopilot device preparation(V2)
- Only Windows 11 supported
- Autopilot V2 currently only works with Windows 11. Companies using Windows 10 cannot use this version.
- We recommend that Upgrading to Windows 11 Catch up as quickly as possible, regardless of whether Autopilot V2 is required.
- No hybrid support (Hybrid Entra ID Join)
- V2 does not currently support a hybrid Entra ID Join, which significantly limits organizations with hybrid IT environments. However, Microsoft is already working on a future solution. More about
- V2 does not currently support a hybrid Entra ID Join, which significantly limits organizations with hybrid IT environments. However, Microsoft is already working on a future solution. More about
- Lack of pre-provisioning and self-deployment mode
- The automated deployment modes “Pre-Provisioning” (also known as White Glove) and “Self-Deploying Mode” known from V1 are currently not available in V2. However, according to Microsoft, these features are planned for future updates.
- The automated deployment modes “Pre-Provisioning” (also known as White Glove) and “Self-Deploying Mode” known from V1 are currently not available in V2. However, according to Microsoft, these features are planned for future updates.
- Limit to personal devices
- By default, devices are registered as personal devices in V2. So-called “corporate device identifiers” (CDI) are required to uniquely identify them as corporate devices. However, this process is currently prone to errors.
- By default, devices are registered as personal devices in V2. So-called “corporate device identifiers” (CDI) are required to uniquely identify them as corporate devices. However, this process is currently prone to errors.
- Maximum 10 apps during device preparation
- The number of applications that can be installed during the out-of-box (OOBE) experience is limited to 10. This could be particularly problematic for larger organizations or more extensive software requirements.
- The number of applications that can be installed during the out-of-box (OOBE) experience is limited to 10. This could be particularly problematic for larger organizations or more extensive software requirements.
- No device-specific name templates
- In V2, there is currently no option to set automated name templates for devices. This feature must be replaced with separate Intune policies.
These restrictions should be carefully examined by companies to decide whether the use of Windows Autopilot V2 makes sense for their respective infrastructure and strategy, or whether parallel use of Windows Autopilot V1 would be advisable for the time being.
4. Comparing Windows Autopilot V1 and Windows Autopilot Device Preparation (V2)
With the introduction of Windows Autopilot V2, Microsoft has introduced a new device deployment method based on a modernized architecture. While V2 brings many benefits and innovations, V1 is still the better choice in certain scenarios. The following comparison shows the most important differences, strengths and weaknesses of both versions and helps to make the right decision for various deployment scenarios.
Strengths of V1:
Windows Autopilot V1 remains the better choice for companies that require hybrid environments, pre-provisioning, or self-deployment. It's also more compatible with a wider range of devices and scenarios.
Strengths of V2:
Autopilot V2 impresses with its modernized architecture, which requires no hardware hashes, as well as improved app management, real-time monitoring and support for sovereign clouds.
recommendation:
Organizations should consider moving to device preparation if they have a cloud-first strategy and don't need hybrid scenarios. Companies with more complex requirements should maintain V1 until all planned features are implemented in V2.
5. Technical requirements and requirements
Hardware and software requirements
Windows Autopilot V2 uses modern operating systems and a compatible IT infrastructure. To successfully implement V2, the minimum requirements are as follows:
- operating system: Windows 11 from version 24H2 (or Windows 11 22H2/23H2 with KB5035942)
- Network connection: A stable Internet connection is required for initial configuration
- Hardware: Devices must be UEFI enabled and it is recommended that you use modern hardware for best results
- Entra ID (formerly AAD): An Entra ID tenant is required for device authentication
Introduction to Windows Autopilot and Windows Autopilot Device Preparation
Windows Autopilot V2 can be optimally integrated into cloud-based IT environments. In the case of hybrids or On-premises solutions However, challenges remain, such as the lack of hybrid support. Organizations should ensure that their endpoint management solutions, particularly Microsoft Intune, are fully compatible to efficiently manage policies, apps, and reports.
SOFTTAILOR helps companies to optimally implement Windows Autopilot and Autopilot Device Preparation — especially in the context of upgrading to Windows 11. Our experts help with strategic planning, implementing complex integrations such as hybrid join configurations or migrating existing ones software distribution systems to Intune. In this way, we enable a smooth transition to modern, efficient and secure device delivery.
6. Future developments: What's to come
Windows Autopilot V2 will be supplemented in the future with significant innovations that further improve device deployment. This includes customizing the out-of-box experience (OOBE) so that IT administrators can personalize it more and name devices based on their organizational structure. Self-deployment and pre-provisioning modes should also return to make device deployment even more flexible and efficient.
Microsoft is also planning to introduce tenant binding to simplify management in multi-tenant environments, as well as extended onboarding via the Windows Company Portal to guide users even better through the set-up process. These advancements strengthen the future security of Autopilot V2 and improve control, security and efficiency in device management in companies.
{{cta-027=” /dev/components "}}
7. Conclusion
Windows Autopilot offers companies a modern and time-saving solution to significantly simplify the complex process of device deployment. In particular, the introduction of Autopilot V2 shows that Microsoft is consistently pursuing its cloud-first strategy. The elimination of hardware hash registration and improved real-time monitoring represent important improvements.
However, key functions such as hybrid support or pre-provisioning are currently limited to version 1, which poses challenges in particular for hybrid IT environments. Companies should therefore check carefully which version better meets their requirements. However, it is clear that Autopilot V2 still offers a lot of development potential and will certainly become even more flexible and comprehensive in the future.
Our experts provide you with know-how and tried and tested solutions to make your IT processes more efficient and secure. Arrange an initial consultation now and we're taking your device deployment to the next level!