An often underestimated weak point in companies' IT security is their own employees and the devices they use.
90% of all successful ransomware attacks Go on poorly or unmanaged devices (so-called endpoints) back. Studies have shown that the risk of Cyber attacks 11 times higher is when more than 20% of endpoints are not properly managed. Endpoints include laptops, cell phones, but also industrial PCs and cash register systems (POS).
Phishing emails, weak passwords, or insecure software — it is often minor carelessness on the part of end users and negligence on the part of the IT department that opens the door to cyber criminals.
But with a well-thought-out endpoint strategy, this risk can be significantly reduced. This turns the biggest vulnerability into a controllable factor — and the company remains protected.
The most important things in brief
- End users as a risk: Carelessness and a lack of security awareness make employees the preferred target for cyber criminals.
- Devices as the biggest lever: Devices connect employees to corporate resources. If they are properly protected from a technical point of view, the attack surface is massively reduced.
- Centralized administration: Unified endpoint management enables centralized control and protection of all end devices. This is how companies keep track of things.
- Proactive security measures: System hardening, regular software updates and the use of an endpoint protection platform close vulnerabilities and prevent attackers from spreading in the system in an emergency.
- Staff training: Targeted security awareness training increases security awareness and reduces the risk of human error.
Human weak spot? We sensitize your users and establish technical and organizational protective measures against cyber attacks.
1. Why are end users the biggest cyber risk?
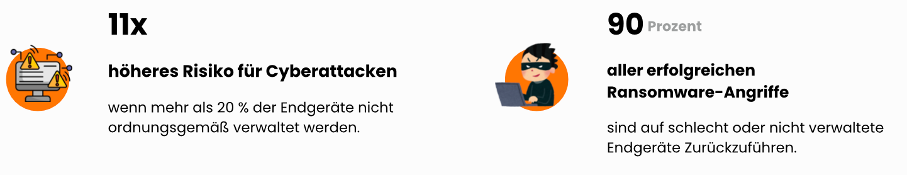
Studies show that 90% of successful ransomware attacks are due to poorly or unmanaged devices. In addition, the risk of cyber attacks increases 11-fold, with more than 20% vs. less than 5% improperly managed devices. Common causes include:
- Phishing and social engineering: Attackers use manipulative techniques to trick employees into revealing confidential information or opening harmful links.
- Weak passwords and lack of MFA: Simple or multiple passwords facilitate unauthorized access to company data. Multi-factor authentication would prevent this.
- Unpatched software: Failures to make regular updates open up security gaps that can be exploited by cyber criminals.
- Missing least privilege and zero trust: Once attackers are in the system, they can often spread undisturbed to the most critical systems and administrator accounts. This can be prevented through technical-organizational concepts such as least privilege and zero trust.
{{example-scenario=” /dev/components "}}
2. How can companies protect themselves?
The market for cybersecurity solutions and services is confusing. That is why SOFTTAILOR has the Endpoint Strategy developed, with the implementation of which companies massively reduce their attack surface and prevent 99% of cyber attacks. The following measures should be taken into account:
1. Unified Endpoint Management (UEM)
Die Unified Endpoint Management (UEM)solution is the control center for managing and securing end devices and is required to implement further measures. It allows you to centrally manage all devices in the company — from laptops to desktops to mobile devices. Installations, configurations and maintenance can be carried out largely automatically, which not only reduces administrative effort, but also ensures compliance with security guidelines and compliance requirements. SOFTTAILOR uses market-leading solutions such as Microsoft Intune, which enable modern security features such as conditional access and zero trust.
2. System hardening
By default, operating systems and applications are not optimally protected against cyber attacks. Windows versions for companies in particular often have the same security configuration “out of the box” as private versions of Windows. Companies must therefore take targeted measures to System hardening grab to minimize the attack surface. This includes deactivating unnecessary functions, restricting user rights, and specifically adjusting safety-critical settings. This includes the introduction of concepts such as Zero Trust and least privilege. Anyone who leaves gaps here acts negligently and increases the risk of successful cyber attacks.
3. Patch Management
Cyber attacks often exploit known vulnerabilities in operating systems and applications. patch management is therefore an essential security measure that ensures that software is regularly updated. But many organizations are not implementing this practice consistently enough — on average, it takes over 100 days before critical security gaps are closed. This is fatal because 60% of all successful cyber attacks can be traced back to unpatched systems. Companies must therefore ensure that updates are imported promptly and that structured patch management is implemented to consistently close security gaps. Tools like Patch My PC and Robopack, for automated patching of standard applications, is just one component.
4. Endpoint Protection Platform
In addition to preventive measures such as patch management and system hardening, Endpoint Protection Platform crucial for identifying and preventing threats in real time. It is the intelligent evolution of classic antivirus. SOFTTAILOR works here Microsoft Defender, which automatically detects, blocks, and successfully repels threats. Thanks to cutting-edge EDR and XDR technologies (Endpoint Detection and Response, Extended Detection and Response) and the use of AI, attacks can be analyzed and stopped in real time — before damage occurs.
{{cta-box=” /dev/components "}}
3. Conclusion: Endpoint management is one of the top priorities of every IT department
End users and devices pose a significant risk to companies' IT security. Due to the sheer number and human component, they are difficult to control and at the same time provide access to the most important company resources.
By implementing a comprehensive Endpoint Strategy, which includes both technical and organizational measures, however, this risk can be significantly reduced. Investments in modern security solutions and continuous employee training pay off in the long term and protect companies from potential cyber threats.
SOFTTAILOR is the only IT service provider focused on endpoint management & security that offers its customers the outsourcing of device management as a holistic Endpoint Management as a Service offers to consistently address every point of the endpoint strategy.
Companies that do not opt for holistic outsourcing are currently particularly common”Patch Management as a Service“rolled out — a service that automates and completely covers the process of installing security-relevant updates. IT departments often don't keep up with this, even though they risk major security gaps and are even required to do so by regulatory and insurance companies for the most part.
A free one now initial consultation appointment agree and bring IT security up to date.